Back to:
Top Teams
InsidePro
Link to original writeup (external, pdf)
Resources
| Members
| 16
|
| Handles
| Admin, -=Cerberus=-, .Scorpio., dda, H0AX, Fzero, Kaiser, lindros,
mastercracker, Mastermind, passcape, POLIMO, Porr3, teraflopgroup,
test0815, Tyra
|
| Software
| Hash Manager / HM Tools, oclHashcat / cudaHashcat,
Extreme GPU Bruteforcer, John the Ripper, Unified List Manager (ULM)
|
| Hardware
| Roughly 100 CPU cores, and roughly 50 graphics cards.
|

Crack Me If You Can 2015
InsidePro Team
Write-up
Preparation
Before the CMIYC competition, we have developed a client for managing
statistics, cracks, left lists, etc. This client was tested in the
HashRunner competition and after a couple of improvements, was ready
for the real test. We had also setup TeamSpeak server for main
communications, a Google spreadsheet for splitting tasks amongst the
team and a forum board for more elaborate messages. Finally, we have
prepared a module to crack the new Argon2 hashes just in case they
would have been part of the contest.
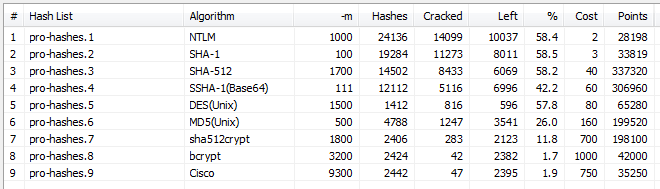
General strategy
Our global strategy pretty much stayed the same: Free for all in the
first 12 hours focusing mainly on the fast hashes and then identify
patterns to apply to the other hash types. Once a pattern is found to
be present in the slow hashes, a group task is created to either
quickly get the cracks out or to quickly see if the pattern is not
worth pursuing.
Contest
Like planned we went for the free for all approach in the first hours
of the contest. However because of the submission format and the fact
that the member responsible for password submission was working at the
beginning of the contest, we were not able to properly submit our
cracked list before around 12 hours into the contest.
It was quickly noted that all passwords contained special/national
characters so one of the approaches was to filter all the wordlists
for only words with at least one of these characters in them. One of
the patterns noticed was the Korean alphabet concatenated together
such as "ieungpieups sangdigeut". We had hits in pretty much all
algorithms with this pattern but the member who got them in the first
place is unknown.
Using all the passwords gotten in the first day of cracking, one of
our members created a custom charset on JTR and got several hits on
various algorithms. The blowfish hashes kept us busy on trying to
find new patterns besides the Korean alphabet. We did have a couple of
passwords with Japanese words concatenated but could not find an
attack with a reasonable keyspace to cover in time and get hits. At
least we got some reasonable amount of hits on the SHA512crypt using a
wordlist with passwords only in $HEX[] format that one of our member
had. This has been the main group task that lasted almost the entire
contest. Finally 2 other approaches did give some good results: 1)
rules that insert special characters at every position of the word and
2) using the random rule generator of oclHashcat.
Last words and comments
First of all, we really want to thank KoreLogic's team for hosting
this great contest again this year. We also found enlightening, the
"About this year's contest" that was published right after the end of
the contest. We can't say that we are now ready for UTF-8 but at least
we have raised our awareness about it. We do understand the logic
behind this contest (and the ones before that) but it did remove a bit
of the fun doing the contest almost exclusively with special
characters which are not that common in the hashes we get in our hands
on yearly. We want also to congratulate Hashcat's team that took the
lead and kept it the whole contest. They were really one notch above
the other teams and we'll all have to improve to get them a better
challenge next time. Congratulations also to Cynosure Prime for being
the best emerging team (O.K., they are the only new team in the pro
section but they did very well).


